In a business environment, “access control” refers to managing who is permitted to use a space or resource. It may sound simple, but access control systems can play a big role in optimizing business operations.
Business owners and operators face a fundamental challenge. The people vital to their success —from managers and workers to customers and suppliers—can inadvertently cause problems. A single lost key could lead to capital costs, revenue losses, increased liability, and more. Read on to see how the ability to control access to your business can not only help protect your business, it can also streamline operations and keep things running smarter.
Different types of access control in a business
Let’s dig a bit deeper into the access control definition. There are two basic access control types: physical and logical.
Physical access control is what limits access to an individual building, campus, equipment or server room, and other physical spaces and assets. The simplest example of physical access control is a key, but in today’s smart business security environments, access control systems often signify a badge and card reader.
Logical access control is the security approach that limits permissions to use computers, networks, system files, and other data owned or maintained by that business. An account password is a perfect example of logical access control security.
Alarm.com for Business provides cloud-based physical security access control that combines intuitive user management with a seamless alarm and video integration. With an Alarm.com business access control system, operators can give employees and visitors the precise level of access they need—protecting sensitive spaces and equipment, while facilitating smoother business operations.
Why keys aren’t enough for physical access control
What’s wrong with a good old-fashioned key? Maybe nothing, in businesses with one location, just a few employees, and one or two doors. But even those businesses often prefer to control access through a security system that integrates multiple functions.
Keys have a few drawbacks when it comes to access control systems. They can be heavy, cumbersome, easy to lose, and a hassle to replace. “Alarm.com research has found that if a business has more than 20 employees, it loses money on keys,” says James Reno, Vice President of Alarm.com Commercial Sales. “Calling a locksmith every time an employee leaves or someone loses a key costs businesses thousands of dollars a year.”
If businesses don’t budget to address the loss of money aspect of key-based access control, they risk current or former employees having access they shouldn’t. So, many businesses discover that it’s far more cost-effective to implement an integrated platform for security, access control, video surveillance, and business automation.
Another drawback of relying on keys for access control security: they don’t offer flexibility. Businesses often need to grant temporary or limited access to temp workers, suppliers, consultants, and others. The logistics of physical keys simply don’t permit that ease of use.
Why keys aren’t enough for physical access control
What’s wrong with a good old-fashioned key? Maybe nothing, in businesses with one location, just a few employees, and one or two doors. But even those businesses often prefer to control access through a security system that integrates multiple functions.
Keys have a few drawbacks when it comes to access control systems. They can be heavy, cumbersome, easy to lose, and a hassle to replace. “Alarm.com research has found that if a business has more than 20 employees, it loses money on keys,” says James Reno, Vice President of Alarm.com Commercial Sales. “Calling a locksmith every time an employee leaves or someone loses a key costs businesses thousands of dollars a year.”
If businesses don’t budget to address the loss of money aspect of key-based access control, they risk current or former employees having access to places they shouldn’t. So, many businesses discover that it’s far more cost-effective to implement an integrated platform for security, access control, video surveillance, and business automation.
Another drawback of relying on keys for access control security: they don’t offer flexibility. Businesses often need to grant temporary or limited access to temp workers, suppliers, consultants, and others. The logistics of physical keys simply don’t permit that ease of use.

What you can do with access control systems in your business
Access control security can be a powerful addition to small business security or a commercial security system, boosting peace of mind while providing valuable insights. While this improvement over key-and-lock replacement is important, management of the entire business is enhanced when access control is integrated with other commercial and small business security products.
Alarm.com’s business security platform includes access control tools and features like multi-site management, swipe to disarm, expiring access, access history reports, reader-based anti-passback support, and bulk user management. Our user-friendly business access control systems can be connected to an Enterprise Dashboard and app, letting business owners and managers easily keep track of who’s coming and going in one view.
Simplified access management: Using the Alarm.com app or website, business operators can add or remove authorized users and cards. Commercial operators enjoy the simplicity of bulk-adding large batches of users at one time or setting an automatic deactivation date for a group that will no longer require access.
Mobile lock control: Mobile access is now widespread, and small business owners in particular will appreciate access control security that allows them to control locks from their mobile device. It’s easy to lock up, unlock, or temporarily buzz someone in from anywhere. And for larger businesses with multiple employees utilizing access control, you can add or revoke mobile permissions—making it easy to manage who’s letting people in.
Automation rules, schedules, and alerts: Whether your business has just one location or hundreds, automating security access control is an easy way to streamline operations. For example, it’s simple to create a rule that automatically disarms the alarm when the first employee badges in for the day, or arms the system with a quick double tap on their way out the door at night. And if someone badges in on the wrong day or time, you’ll get an unexpected activity alert to let you know.
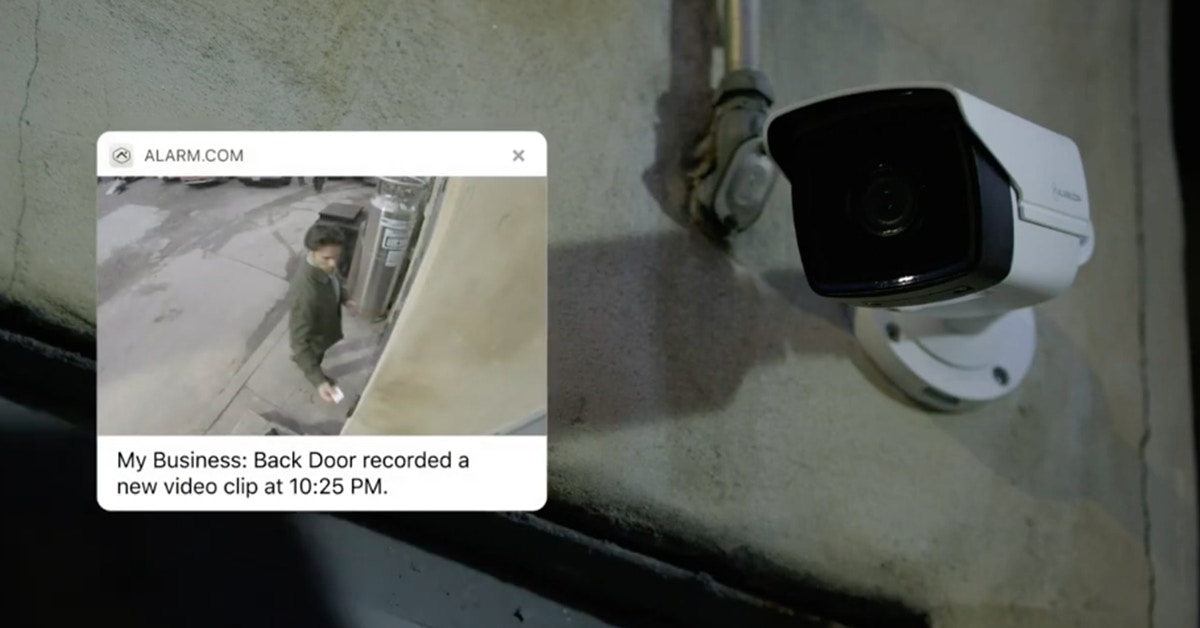
Seamlessly integrated video: When video surveillance and business security cameras are integrated with an access control system, it opens a new world of insights. With a video doorbell, for example, you can interact with a visitor and buzz them in remotely. Want to see what happened during an access control event? The Alarm.com app and dashboard takes you to the corresponding video with a single tap. And our video-driven Business Activity Analytics feature can help with staffing and other decisions that all hinge on who’s been granted access at any given time. You’ll also be able to visualize employee movement throughout the building once they’ve entered with contract tracing.
When combined with intrusion, video, and energy, Alarm.com’s smarter access control serves as an all-in-one security solution for managing access to business properties.
How access control security works in physical spaces
The seamless integration of access control within the Alarm.com platform helps business owners and operators stay secure, while giving them new awareness into access events and key operational activities. Let’s explore how integrated access control functions across a few different real-life scenarios:
In a medical practice: Dr. Hoffman wakes up to an alert showing his office manager accessed the front door early in the morning, so he knows the practice will open on time that day.
- A video clip provides visual verification that the early arrival is an employee.
- The employee unlocks the door and disarms the security system with a single swipe of her badge.
- The “First Person In” rule Dr. Hoffman created automatically locks or unlocks the front door based on practice hours.
At a multi-location retail store: Regional manager Meg is setting up access for 15 new seasonal employees starting next week.
- Meg uses the bulk user upload feature to easily add in and apply the new employees to their designated locations.
- Newly hired managers and employees receive different levels of access privilege.
- Meg schedules the new cards to start working the same day the new employees do.
At a high school STEM program: IT manager Naveen is monitoring the science wing and gets an unusual activity alert for the chemistry lab.
- Naveen pulls up the access activity page and filters the results to show lab door activity.
- He finds the unexpected access and clicks through to the stream video recorder (SVR) clip that shows an employee stealing lab equipment.
- Naveen immediately revokes the employee’s access control permissions in real time, and one year of the employee’s access history is exported for school records. ?? Not clear
At a local coffee shop: At the end of a busy day, owner Amelia can easily close shop with the push of a single button in her mobile app.
- The front, back, stock room, and office doors lock, and the neon “We’re Open” sign in the window turns off.
- The thermostat adjusts the overnight temperature to save energy.
- The security system arms to “away” status.
Using security access control to further streamline operations through mobile apps
We’ve already seen how mobile lock control can make life easier when your security system features access control. Now, Alarm.com is expanding the power of mobile to include the employees and others with regular access to that business.
With Alarm.com’s access control Mobile Credentials feature, you can eliminate the need for separate physical access badges and key fobs, which can be easily stolen or misplaced, and which still require activation and programming.
Instead, employees and visitors can badge in with a swipe of their mobile phones, without having to worry about forgetting their badge or losing their fob. Business owners or managers can send a text-based mobile credential invitation to an employee, they can install the Alarm.com app, and their phone now serves as their access card. Mobile Credentials are compatible with both iOS and Android phones, work exclusively with Alarm.com readers, and don’t require user logins. The user simply holds their phone near the reader to be granted access.

For business owners interested in Mobile Credentials, rest assured—you won’t need to start from scratch. Alarm.com offers the latest access control technology, with three new card readers that allow you to maintain existing user credentials, while transitioning to encrypted smart credentials for enhanced business security.
How to get access control systems in your business
Alarm.com for Business access control security integrates with leading hardware brands, so business owners and operators won’t have to replace locks and card readers or install expensive new hardware. Alarm.com setup is plug-and-play with a cloud-based platform—no on-site server or IT department required.
Alarm.com gives you extra protection and efficiency by integrating access, intrusion, and video monitoring into one intuitive solution. Give your business the benefit of smarter access control today.
